Percipient-IoT
Percipient-IoT is an innovative provider for IoT and IIoT solutions. This frequently involves IoT cellular connectivity that enables manufacturers, oil & gas, and other industries to deploy differentiated technologies that often disrupt their markets by vastly improving their performance and achieving a higher level of success in competitive markets.
Internet of Things (IoT) and Industrial Internet of Things (IIoT) have become high grow business segments. It is expected that there will be an exponential demand for IIoT devices globally deployed. Everything will be connected to the internet through IoT on a massive scale. 5G Ultra Wide-band will enable these demands to occur on the network bandwidth. IIoT is critically important because it will be a major technology that enable much lower costs and improved quality in manufacturing. For those manufacturing companies that utilize IIoT, they will have a significant competitive advantage over those that do not deploy IIoT.

IoT and IIoT represents the next great trend in the evolution of technology. Percipient-IoT is used to represent the network of physical objects, such as machines used for manufacturing, oil & gas, medicine and healthcare. However, for industrial applications, Industrial Internet of Things (IIoT) is an extension of IoT that includes industrial applications, such as robotics, medical devices and software-defined manufacturing processes. IoT is used to provide customer benefits, that is often included in smart-devices. IIoT is deployed in industrial manufacturing production operations to enable faster and more accurate decision-making.
The Majestic


Healthcare IIoT
Healthcare IIoT application have become an essential foundation for medical care. Medical devices and Information Technologies are present is all large hospitals and operating rooms. The enable the doctors and nurses with the information needed to interact rapidly and provide the best care possible. IoT solutions enable all medical devices to be connected and monitored in real time. This requires dynamic network connectivity, since these devices are always communicating with each other. Network Connectivity is achieved through access points, routers and gateways. The networks must be completely reliable and provide for very minimum latency.
Critical health care networks must provide for 100% connectivity and have build in redundant connectivity that enables fail-over in the event of an unlikely disruptancy. The information provided over the network is essential and critical to any healthcare IT infra-structure. The healthcare network must be secure and work all the time. Wireless WiFi has become ubiquitous for deploying and healthcare reliable network with very low latency.


Industrial IoT for Manufacturing.
Percipient IoT designs and deploys both IoT in products and IIoT used in factory machines. All of the applications have multiple low-cost sensors that connect to wireless networks and stream data to the cloud where it is run through Artificial Intelligence-Machine-Learning (AI-ML) algorithms to control and make-decisions to make manufacturing and business processes much more efficient. IIoT is being used to transform manufacturing by providing extensive data that is streamed in real time.
The Greatest American Hero Theme Song
The industrial internet of things (IIoT) is the use of smart sensors and actuators to enhance manufacturing and industrial processes. Also known as the industrial internet or Industry 4.0, IIoT uses the power of smart machines and real-time analytics to take advantage of the data that "dumb machines" have produced in industrial settings for years. The driving philosophy behind IIoT is that smart machines are not only better than humans at capturing and analyzing data in real time, but they're also better at communicating important information that can be used to drive business decisions faster and more accurately.
Operational Technology (OT)
The networks that control industrial control systems process is referred to as OT. One of the major challenges with OT is the vulnerability of these systems. They are becoming targets for sophisticated malware that is often overlooked. Malware is can be used to breach OT used for fabrication equipment, human-machine interfaces, automated material handling systems and other automated processes. OT breaches are often successful when there are multiple unpatched window systems. Examples of malware that have been used to breach OT include Conficker and WannaCry. To prevent OT breaches, it is necessary to maintain secure configurations and allow only specified users administrative privileges. Unused software should be removed and unused ports disabled. Insecure configuration of endpoint opens vulnerabilities for exploitation for self-propagating malware. Continuous Vulnerability Management is essential to reduce the likelihood of vulnerability exploitation, as well as insuring patches are applied as soon as possible.

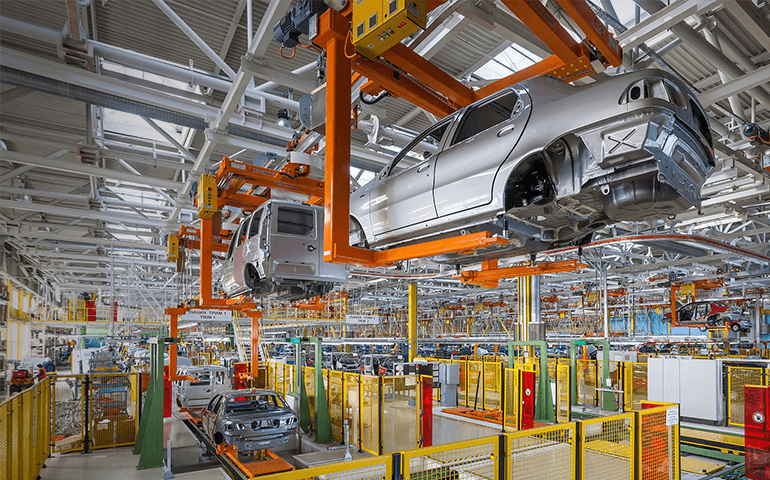
Connected sensors and actuators enable companies to pick up on inefficiencies and problems sooner and save time and money, while supporting business intelligence efforts. In manufacturing, specifically, IIoT holds great potential for quality control, sustainable and green practices, supply chain traceability, and overall supply chain efficiency. In an industrial setting, IIoT is key to processes such as predictive maintenance (PdM), enhanced field service, energy management and asset tracking.

IIoT is a network of intelligent devices connected to form systems that monitor, collect, exchange and analyze data. Each industrial IIoT ecosystem consists of:
- connected devices that can sense, communicate and store information about themselves;
- public and/or private data communications infrastructure;
- analytics and applications that generate business information from raw data;
- storage for the data that is generated by the IIoT devices; and
These edge devices and intelligent assets transmit information directly to the data communications infrastructure, where it's converted into actionable information on how a certain piece of machinery is operating. This information can be used for predictive maintenance, as well as to optimize business processes.
By using AI-ML to learn and analyze the data received from the sensors, IIoT can enable greater insight into processes and make them more efficient. IIoT reduces unexpected down-time.
With a strong focus on machine-to-machine (M2M) communication, big data and machine learning, the IIoT enables industries and enterprises to have better efficiency and reliability in their operations. The IIoT encompasses industrial applications, including robotics, medical devices, and software-defined production processes.


The IIoT goes beyond the normal consumer devices and internetworking of physical devices usually associated with the IoT. What makes it distinct is the intersection of information technology (IT) and operational technology (OT). OT refers to the networking of operational processes and industrial control systems (ICSs), including human machine interfaces (HMIs), supervisory control and data acquisition (SCADA) systems, distributed control systems (DCSs), and programmable logic controllers (PLCs).
Holding out for a Hero
The convergence of IT and OT provides industries with greater system integration in terms of automation and optimization, as well as better visibility of the supply chain and logistics. The monitoring and control of physical infrastructures in industrial operations, such as in agriculture, healthcare, manufacturing, transportation, and utilities, are made easier through the use of smart sensors and actuators as well as remote access and control.
In the context of the fourth industrial revolution, IIoT is integral to how cyber-physical systems and production processes are set to transform with the help of big data and analytics. Real-time data from sensors and other information sources helps industrial devices and infrastructures in their “decision-making,” in coming up with insights and specific actions. Machines are further enabled to take on and automate tasks that previous industrial revolutions could not handle. In a broader context, the IIoT is crucial to use cases related to connected ecosystems or environments, such as how factories become smart factories.


The consistent capturing and transmitting of data among smart devices and machines provide industries and enterprises with many growth opportunities. The data allows industries and enterprises to pick up on errors or inefficiencies in the supply chain, for example, and immediately address them, thus pushing for day-to-day efficiency in operations and finance. Proper integration of the IIoT can also optimize the use of assets, predict points of failure, and even trigger maintenance processes autonomously.
By adopting connected and smart devices, businesses are enabled to gather and analyze greater amounts of data at greater speeds. Not only will this enhance scalability and performance, but it can also bridge the gap between the production floors and general offices. Integration of the IIoT can give industrial entities a more accurate view of how their operations are moving along and help them make informed business decisions.
Adoption of the IIoT can revolutionize how industries operate, but there is the challenge of having strategies in place to boost digital transformation efforts while maintaining security amid increased connectivity.
All through the night


Industries and enterprises that handle operational technologies can be expected to be well-versed in such aspects as worker safety and product quality. However, given that OT is being integrated into the internet, organizations are seeing the introduction of more intelligent and automated machines at work, which in turn invites a slew of new challenges that would require understanding of the IIoT’s inner workings.
Neil-Diamond-Sweet-Caroline
With IIoT implementations, three areas need to be focused on: availability, scalability, and security. Availability and scalability may already be second nature to industrial operations, since they could already have been established or in the business for quite some time. Security, however, is where many can stumble when integrating the IIoT into their operations. For one thing, many businesses still use legacy systems and processes. Many of these have been in operation for decades and thus remain unaltered, thereby complicating the adoption of new technologies.

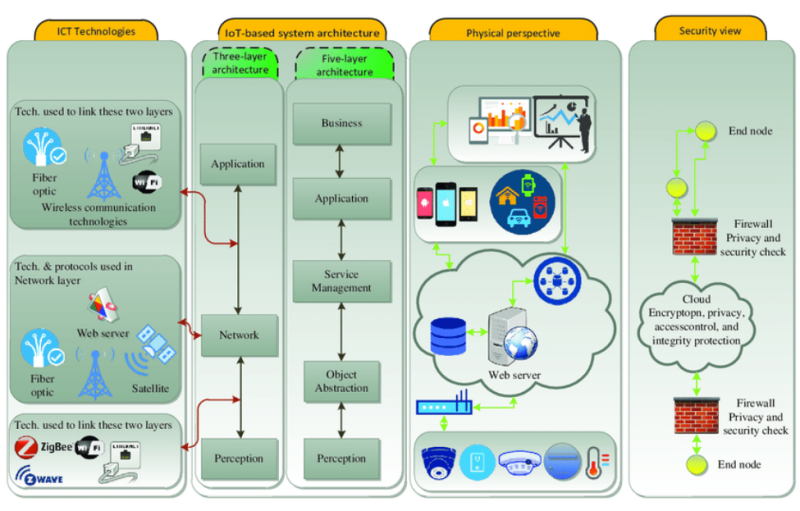
The proliferation of smart devices has given rise to security vulnerabilities and the concern of security accountability. IIoT adopters have the de facto responsibility of securing the setup and use of their connected devices, but device manufacturers have the obligation of protecting their consumers when they roll out their products. Manufacturers should be able to ensure the security of the users and provide preventive measures or remediation when security issues arise.
Even more, the need for cybersecurity is brought to the fore as more significant security incidents surface over the years. Hackers gaining access to connected systems do not only mean exposing the business to a major breach, but also mean potentially subjecting operations to a shutdown. To a certain extent, industries and enterprises adopting the IIoT have to plan and operate like technology companies in order to manage both physical and digital components securely.
Everything counts
Adopters are also faced with the challenge of properly integrating industrial operations with IT, where both connection and information need to be secured. While gathered data plays an important role in generating insights for the devices and infrastructures, it is imperative that personal information be segregated from general log data. Information like personally identifiable information (PII) should be stored in an encrypted database. Storing unencrypted information together with other relevant activity in the cloud could mean businesses running the risk of exposure.
Oil and Gas IIoT
The Industrial Internet of Things (IIoT) has been fueling digital transitions for nearly every global industry. The oil and gas sector is no exception either.
Companies, which gave off the typical old-decade vibe, are gradually coming up a notch to identify Connectivity as an essential growth driver, and embracing IoT to build intelligent and fully mobile factories. The ‘dinosaur’ sentiment is indeed changing.
However, to say that the oil and gas industry has started to adopt digitization only recently would be wrong. Truth be told, a digital headwind surged over the industry in the 1990s and the early part of the century, but unfortunately, failed to change the face of it. For the most part, enterprises were ignorant of the range of opportunities that data could offer if used meaningfully.
Cut to present, the oil and gas industry has reached the cusp of an unprecedented digital boom. It’s riding high on the IIoT wave and leveraging its growth to an extent that it might outwit other capital-intensive industries in the process. Below are five ways in which IIoT is revolutionizing the oil and gas industry, and cementing its foundation to compete in the hydra digital-first world.

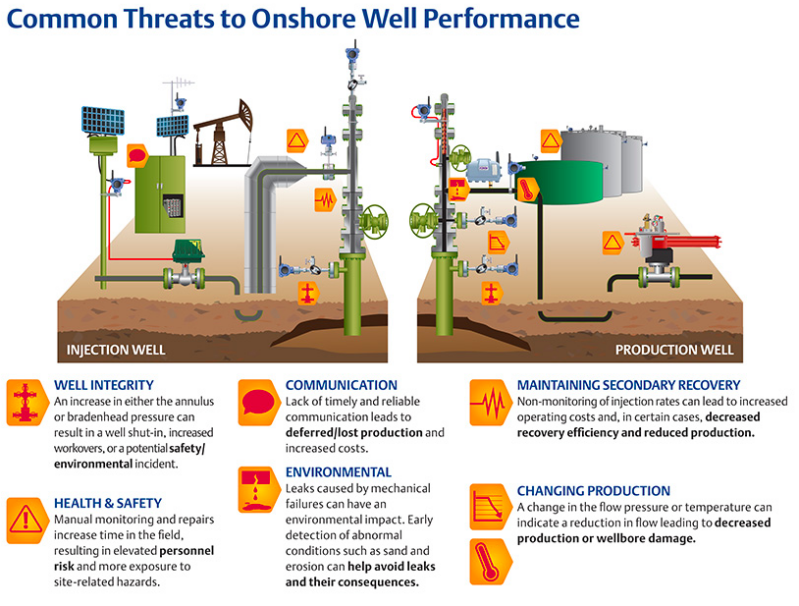

- Creating a Collaborative Ecosystem
IIoT adoption has opened new and advanced frontiers of collaborative innovation for the oil and gas industry. The introduction of integrated digital platforms has fostered an ecosystem where strategic communications no longer sit in silos, rather travel across workstreams to help enterprises enhance collaboration and ensure factory visibility at scale. Integrating an all-access information layer for cross-functional units helps enterprises bear the fruits of competitive benefits, including maximized innovation, strategic decision making, and reduced costs.
Further, creating an IIoT-driven collaborative ecosystem also propagates the concept of Connected Workers in the organizations. Employees using smartphones, wearables, and other connected devices execute tasks with safety and efficiency while harnessing the power of real-time insights. This contributes to building workplace resilience with enhanced performance and auditability, deriving sustained business value out of massively diverse operations.
- Production and Capital Throughput
The proliferation of IIoT in the oil and gas industry has greatly increased production throughput and efficiency, while also enhancing safety and taming overhead costs. The use of wireless sensors and automated monitoring systems, responsible for acquiring, analyzing, and organizing data, have been instrumental in enabling this performance acceleration.
Using real-time data, enterprises are increasingly capable of gaining end-to-end visibility into their on-ground processes, determining qualitative as well as quantifiable understanding around their asset and performance maturity, and making informed decisions to improve field operations.
3. Equipment and Asset Management
IIoT implementation has made it easier for the enterprises to determine the serviceable life of the assets and reconfigure them to avoid performance downtimes. Since sensors continually monitor each functional wheel for anomalies and relay data to maintenance teams, organizations can respond faster to any imminent glitch that might throw stability in flux, thereby ensuring continuous delivery and with impact.
-Billy Ocean - When the Going Gets Tough, The Tough Get Going
4. Remote Performance Monitoring
Given the extensive, multi-location footprint of oil and gas companies, there is always a critical yet daunting need to evaluate asset performance remotely for efficiency, safety, and maintenance needs. Contrary to isolated, unconnected factories of the past, the new-age IIoT-led enterprises have transformed the upstream operations using the sensors and remote controlled devices. These technologies monitor remote assets in real-time, communicate performance data across a common information layer, and help service teams better understand on-ground operations. Metrics, such as pressure and temperature are tracked to monitor the shop floor habitats and are further compared to determine the maximum outputs and operational lags if any.

5. Preventive Maintenance
So far, it’s apparently clear that performance tracking is central to IIoT’s disruptive agenda. Oil and gas companies can examine data to quickly locate the areas of trouble, fix them, and keep things in the usual order. However, IIoT isn’t only helpful in transforming the present, but also in predicting the future. In IIoT’s terms, the process is referred to as Preventive Maintenance, where data insights are used to analyze the infrastructural health and predict problems and failures that might put the operations under stress.


Preventive Maintenance help enterprises spot anomalies in the asset and equipment usage beforehand and initiate pre-emptive action to control damage. Given this, organizations find themselves in a win-win position, where they are able to develop bespoke counteractive strategies for every fault they detect and keep workflows stable. Ultimately, this results in improved efficiency, reliability and reduced operational costs.
-Carly Simon - You Know What To Do
By installing micro sensors on preexisting machinery, Oil and Gas companies can gain unlimited access to a pool of data describing system health in real-time, allowing operators to become intuitive to the network's ebb and flow and making it possible to pinpoint skewed numbers. Real-time performance analytics distance business owners from the expense of damage control while catalyzing production.
Not only will business owners experience a decline in system failures, but also a decrease in on-site accidents. There is an inherent risk associated with the oil and gas industry; the operation is dangerous and easily corruptible. In the past, we have seen oil rig explosions, exposure to toxins, workers falling from extreme heights—it is not an easy environment to work in. Because many of these accidents occur due to system error, IIoT preventative analytics have the potential to greatly reduce these accidents, minimizing lawsuits based on gross negligence.
Remote Monitoring
This is how IIoT tackles human capital management. As the aging workforce enters retirement, they will be replaced by IIoT remote monitoring centers, off-site facilities where operators process incoming data from the microprocessors. This is also a means of reducing accidents; if fewer workers are subjected to the risks of such a caustic work environment, inevitably there will be less accidents and injuries.
The average oil rig worker makes 100k/year, a salary scaled to the risks and niche skillset required to do the job. Perhaps, as the aging workforce dissipates organically and we discover new applications for the big data propagated through IIoT networks, Oil and Gas companies will be able to downsize their workforce while still maintaining the same rate of production. M2M collaboration across an IIoT is not a human replacement, but a supplement rather. We are not replacing humans with machines; we are simply enhancing understanding with absolute human to machine collaboration and helping experts do their jobs more efficiently.
By sending analytics from offshore rigs, directly to a mobile device, workers can respond to data remotely, managing system adjustments without physically being there. This access comes from a custom dashboard that corresponds with all microprocessors.
Asset Management
Oil and Gas cultivation comes with natural limitations, an organic but finite asset, and for this reason asset management is imperative for the oil and gas industry. Although the public awareness of fossil fuel scarcity is at its peak, the rate of excavation is as well. Every year, we see emerging technologies that allow oil rig operations to drill faster and with greater accuracy—multi-well pads, mobile rigs, electrically powered rigs.
IIoT Interconnectivity
The IIoT creates interconnectivity between these technologies, providing a platform for them to converse. In supporting M2M communication, oil and gas enterprises will be able to access minute by minute data illustrating productivity and mapping out the life cycle of each well, while simultaneously determining the coordinates of oil-rich reservoirs to drill into next. Not only, does the IIoT provide inventory management, but also helps operators decide when it's time to move on.
Machine to machine communication is the IIoT's selling point, but I find it also improves human to human communication as well. Human communication is one of the greatest barriers to enterprise in general because it often goes overlooked, especially for companies with a large, international workforce. The IIoT has the potential to bridge gaps in communication between workers by funneling data into a user-friendly dashboard that can be accessed from anywhere. Granting all workers access to the same data pool will eliminate departmental divide and foster a unified vision to carry into practice, helping the whole system run more cohesively, humans and machines alike.
Of course, we are still uncovering ways to apply IIoT big data, and to be frank, there are some technologies the oil and gas industry does not know how to apply yet. Nevertheless, it is better to be at a surplus than a deficit, and for the first time in a while, the oil and gas industry has access to more numbers than they know how to process.
IIoT Security.
Businesses may have grown familiar with the probable business impact of having IT systems go down because of cybercrime or malware infection. However, the convergence of IT and OT introduces a new significant risk factor: real-world threats that could affect even civilians.
Technology fragmentation, and IIoT, by extension, isn’t exempt from the coexistence of different standards, protocols, and architectures. The varying use in IIoT systems, for example, of standards and protocols such as Message Queuing Telemetry Transport (MQTT) and Constrained Application Protocol (CoAP) may hinder IIoT systems’ interoperability.
Many security problems associated with the IIoT stem from a lack of basic security measures in place. Security gaps like exposed ports, inadequate authentication practices, and obsolete applications contribute to the emergence of risks. Combine these with having the network directly connected to the internet and more potential risks are invited.
Unsecure IIoT systems can lead to operational disruption and monetary loss, among other considerable consequences. More connected environments mean more security risks, such as:
- Software vulnerabilities that can be exploited to attack systems.
- internet-connected devices and systems.
- Malicious activities like hacking, targeted attacks, and data breaches.
- System manipulation that can cause operational disruption (e.g., product recalls) or sabotage processes (e.g., production line stoppage).
- System malfunction that can result in damage of devices and physical facilities or injury to operators or people nearby.
- OT systems held for extortion, as compromised through the IT environment.

While pushing for productivity in operations is essential for IIoT systems, security should be regarded as much. Connecting OT to the internet could make businesses more viable, with the help of the many sensors and connected devices at work and the real-time data that they generate. But failing to invest in cybersecurity could undermine the benefits. This is where security by design and embedded security approaches should come in.
Having a security operations center (SOC) is critical in proactively monitoring and defending against the broad range of threats that affect connected environments. This centralized unit allows industries and enterprises to oversee the significant number of alerts that they may encounter and to enable quick response. SOCs are especially beneficial for facilities in need of better visibility and continuous analysis of their security posture. It is the goal of SOC teams to detect security incidents or any anomalous activity and be able to immediately address issues before any compromise could occur. This approach addresses the challenges that could come with legacy systems, low system visibility, and slow response times. With an SOC, alerts will be prioritized and threat correlation will be more optimized to enable enterprises to manage both IT and OT.

However, shifts in the threat landscape as well as industrial infrastructures require organizations to adapt their protection for the new and unknown threats that they may encounter.
Having a full stack of protection purposely built into the different layers of IIoT implementations would enable industries and enterprises to securely conduct their operations. These security layers include the device, the network, and the cloud.
The device layer usually comprises the IIoT devices and applications that are brought in from different manufacturers and service providers. IIoT adopters should be able to know how their manufacturers and service providers transmit and store data. And in the event of a security issue, manufacturers and service providers should also be able to actively notify enterprises of what needs to be addressed.
On the network area, there is the gateway, which gathers data from devices. This is the part where organizations should have next-generation intrusion prevention systems (IPSs) in order for them to monitor and detect potential attacks. The gateway is also where there is usually a control center that issues commands to different devices. The control center is the most critical place where organizations should implement security hardening to ensure protection against malware infection or hackers gaining control of it.


The cloud is where providers should have security implementations that run server-based protection to mitigate the risk of hackers taking advantage of servers and stored data. This reiterates the concern that organizations are subject to applicable data protection retributions.
-Desireless - Voyage Voyage
Securing IIoT systems therefore requires connected threat defense and end-to-end protection from the gateway to the endpoint, that are able to provide:
- Regular monitoring and detection in case of malware infection.
- Better threat visibility and early detection of anomalies.
- Proactive prevention of threats and attacks between IT and OT.
- Secure data transfer.
- A next-generation IPS to prevent attacks from exploiting vulnerabilities.
- Server and application protection across the data center and the cloud.


IoT uses sensors to connect the machines and products through the cloud to the internet networks so that data can be exchanged between these devices and systems over the web. Some examples where IoT is used are products, such as smart-watches, smart-fire alarms, smart-medical sensors, and smart-security systems. These are just a few example where IoT has been integrated into common customer products.